How to Centrally Manage AWS Root Access: Best Practices for Enhanced Security and Governance

Do you manage more than one AWS account? If you’re following AWS’s best practices for multi-account design, chances are you have several accounts—all managed under an AWS Organisation. You’ve likely gone into each account to configure a strong password and enable Multi-Factor Authentication (MFA), guided by alerts from AWS Security Hub.
This approach, however, can become unwieldy and time-consuming, especially when provisioning new accounts.
Fortunately, AWS has introduced new features to make this process centralised, automated, and more secure.
It’s simply the email address you used to create your AWS account. This account has unrestricted access to all resources and settings, making it critical to manage securely.
Introducing AWS’s New Centralised Root Access Management Capability
By leveraging AWS Organisations, we can now centrally secure the root user credentials across all AWS accounts within the organisation. This new capability enables us to:
- Eliminate root user credentials in member accounts, removing the risk of long-term privileged credentials.
- Streamline the creation of secure AWS accounts from the outset, avoiding the need to configure a password and MFA for each new account.
- Prevent the "forgot password" recovery flow for root users, stopping unauthorised attempts to gain access to the account.
- Use a single root user and MFA key for all accounts, simplifying management and enhancing security.
How to Centralise Root Access Management
To enable centralised root access management, follow these steps:
- Log in to your AWS organisation’s management account (the top level account in your AWS organisation).
- Go to the IAM Dashboard and then Root access management
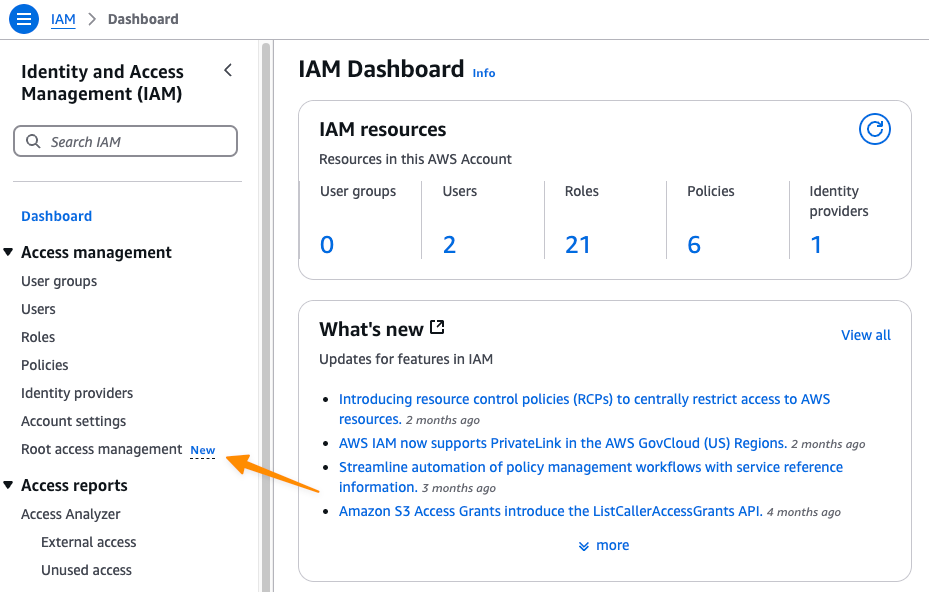
- Click Enable
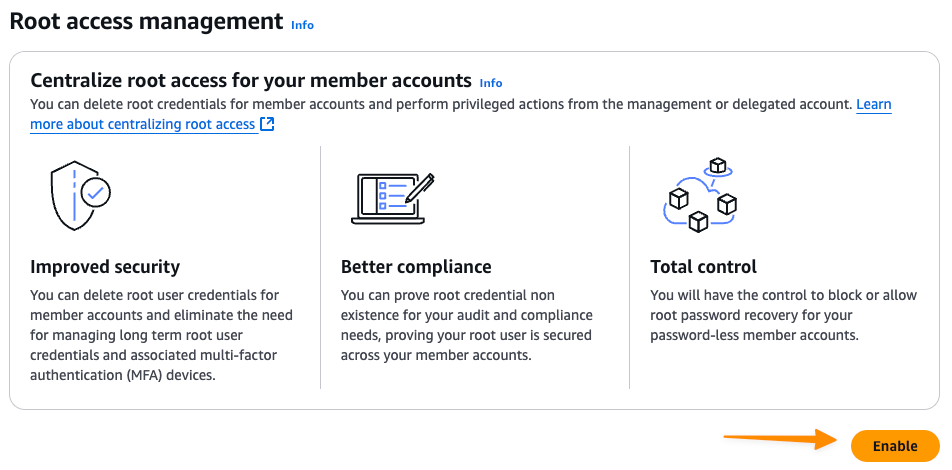
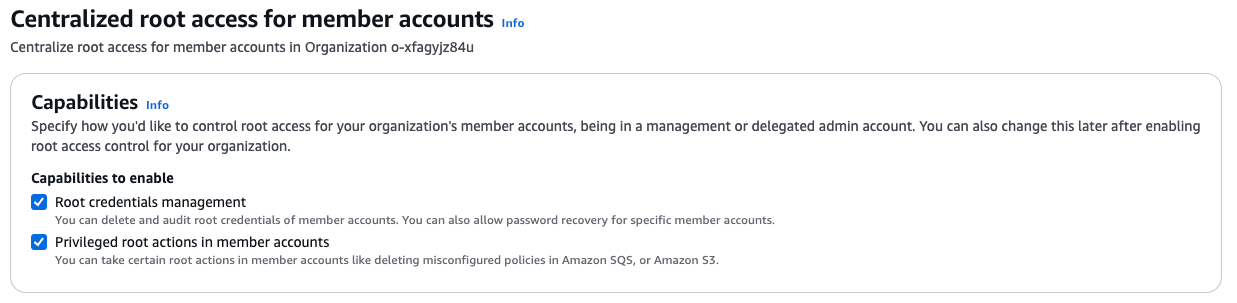
- For Capabilities, enable both Root credentials management and Privilege root accounts in member accounts.
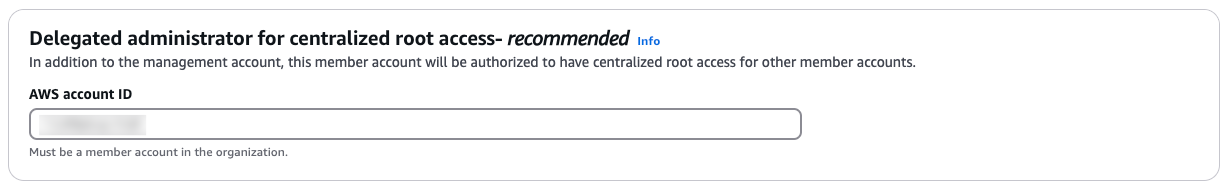
- While optional, I highly recommend enabling this step. It allows you to designate a second AWS account (another root user) to have delegated access to manage centralised root access controls.
For this, select a security-focused account or the account where you typically manage administrative functions. This adds an extra layer of security and redundancy, ensuring your centralised controls remain accessible even if there’s an issue with the primary account.
- Click Enable

Now that everything is enabled, if you want to change any of the settings that you configured, you can do this from the Account Settings page.
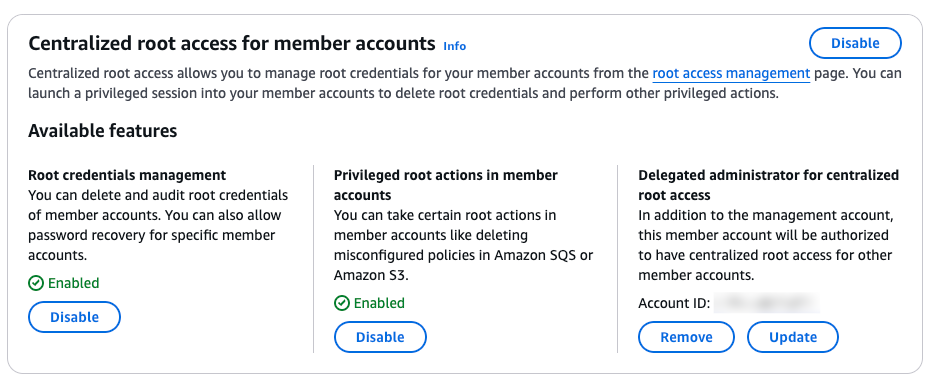
Actions Available with Root Access Management
After enabling Root Access Management, you can perform privileged actions on your member root accounts. As this is a new feature, the available actions are currently limited, but AWS plans to expand these options in the future.
At the time of writing, the following actions are supported:
- Delete S3 Bucket Policy: If an S3 bucket policy is misconfigured and denies access to users within your account, the root account can delete this policy to restore access.
- Delete SQS Queue Policy: Similar to S3 bucket policies, this allows you to delete misconfigured SQS Queue policies that block access.
- Delete Root User Credentials: Remove the root user credentials from an account, eliminating the risk associated with long-term privileged credentials.
Deleting Root User Credentials
- On the Root Access Management console, locate the account for which you want to remove the root user credentials. Then, select Take Privileged Action.
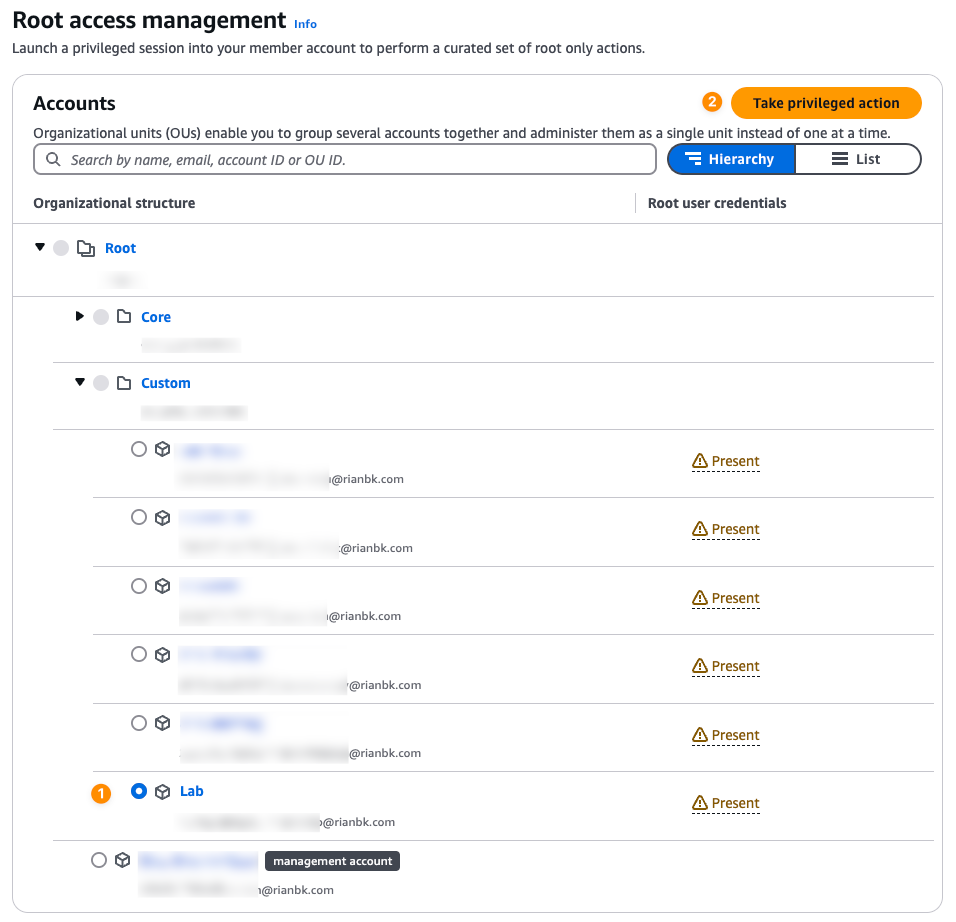
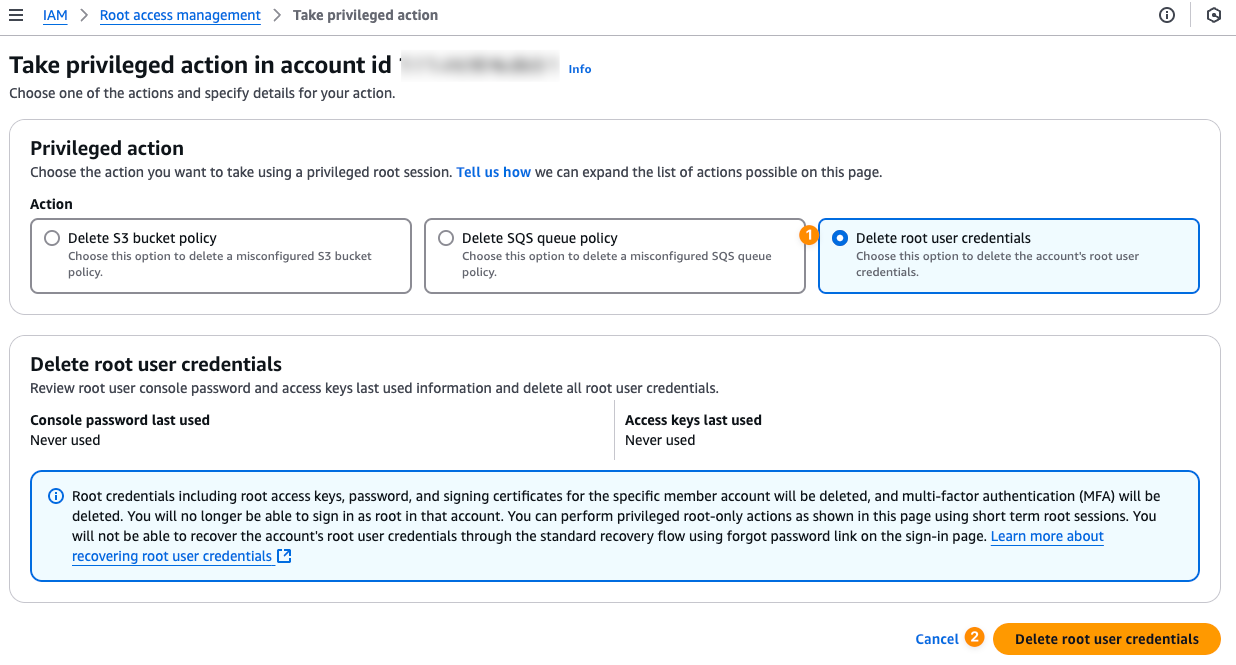
- Select Delete Root User Credentials. You’ll be provided with a report showing whether the root console password or access keys have been used. Once you’ve reviewed the report, click Delete Root User Credentials.
- The console will now indicate that this account no longer has root user credentials present.
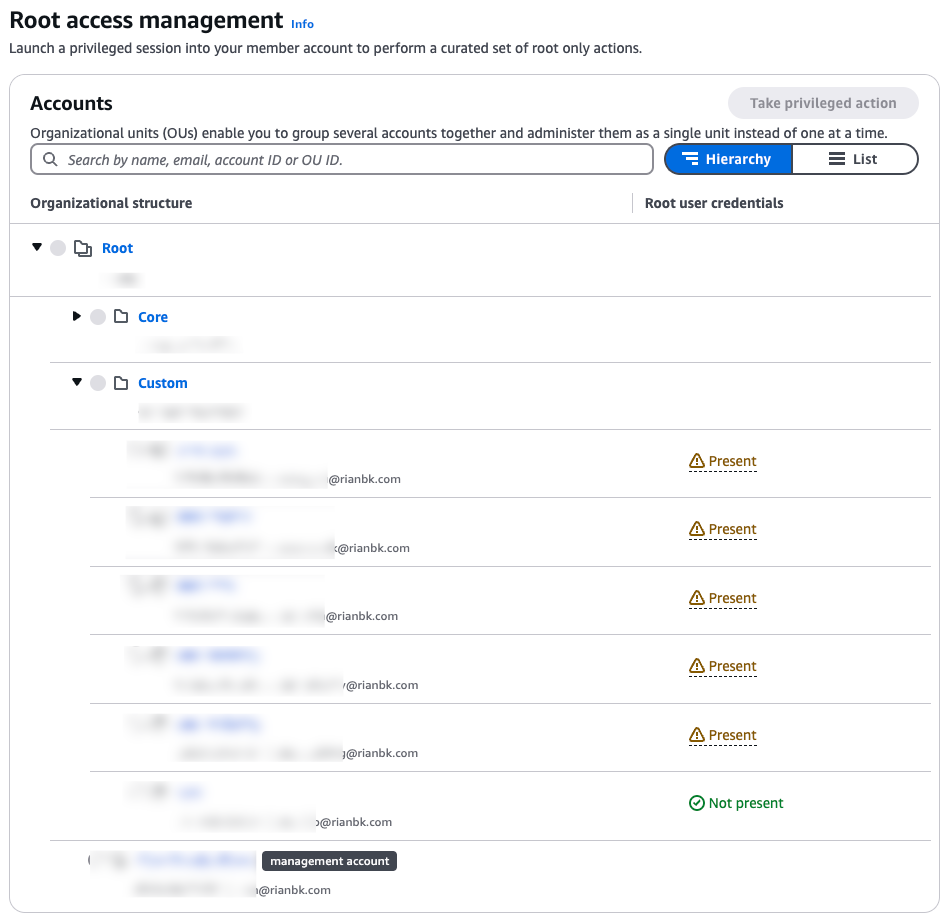
- Repeat this process for each remaining account until the root user credentials have been removed from all member accounts.
Things to know
Here are a few important things to know about Root Access Management.
New AWS Accounts
When you create new accounts through AWS Organisations, they will automatically be created without root user credentials and will be managed by Root Access Management.
Root User Access
If you need to perform an action that requires root user access in a member account, you can temporarily enable Allow Password Recovery for the account using the Take Privileged Action menu. This will allow you to initiate a password reset request, which will send a reset email to the root account’s registered email address. Its also recommended that you delete the Root User Credentials once your done.
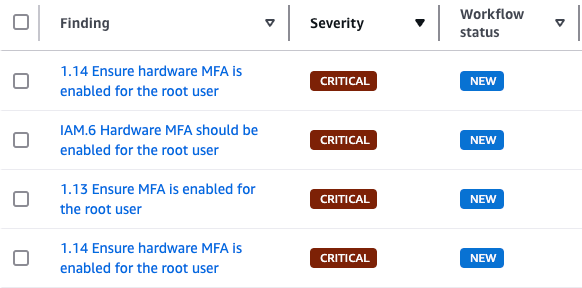
Security Hub
It’s worth noting that Security Hub’s findings and best practices haven’t been updated to recognise this feature yet. As a result, you may still see alerts about the root user account not having MFA enabled.
Final Thoughts on Root Access Management
Centralised Root Access Management simplifies and secures AWS root access across all your accounts. By enabling these features, you eliminate long-term root credentials, streamline account creation, and can perform privileged actions without using the root user account. It’s a small step that delivers significant security and management benefits and well worth implementing today.
Comments ()