Simplifying Infrastructure Automation with AWS CloudFormation Git Sync
Explore a new feature in AWS CloudFormation: Git Sync. This guide provides a look at how Git Sync offers a streamlined approach to automating Infrastructure as Code (IaC) deployments directly from Git repositories.
AWS has released a new way of automating the deployment of CloudFormation Infrastructure as Code (IaC), with Git Sync. Let's see what it can do.
Infrastructure as Code
Infrastructure as Code (IaC) allows you to automate the provisioning and management of your architecture through code. The benefits of this are many, but some key ones are:
- Enhanced collaboration between teams using standard source control tools
- Automated deployment reducing manual errors through "ClickOps"
- Integration with tools to scan your configuration for security or best practice issues
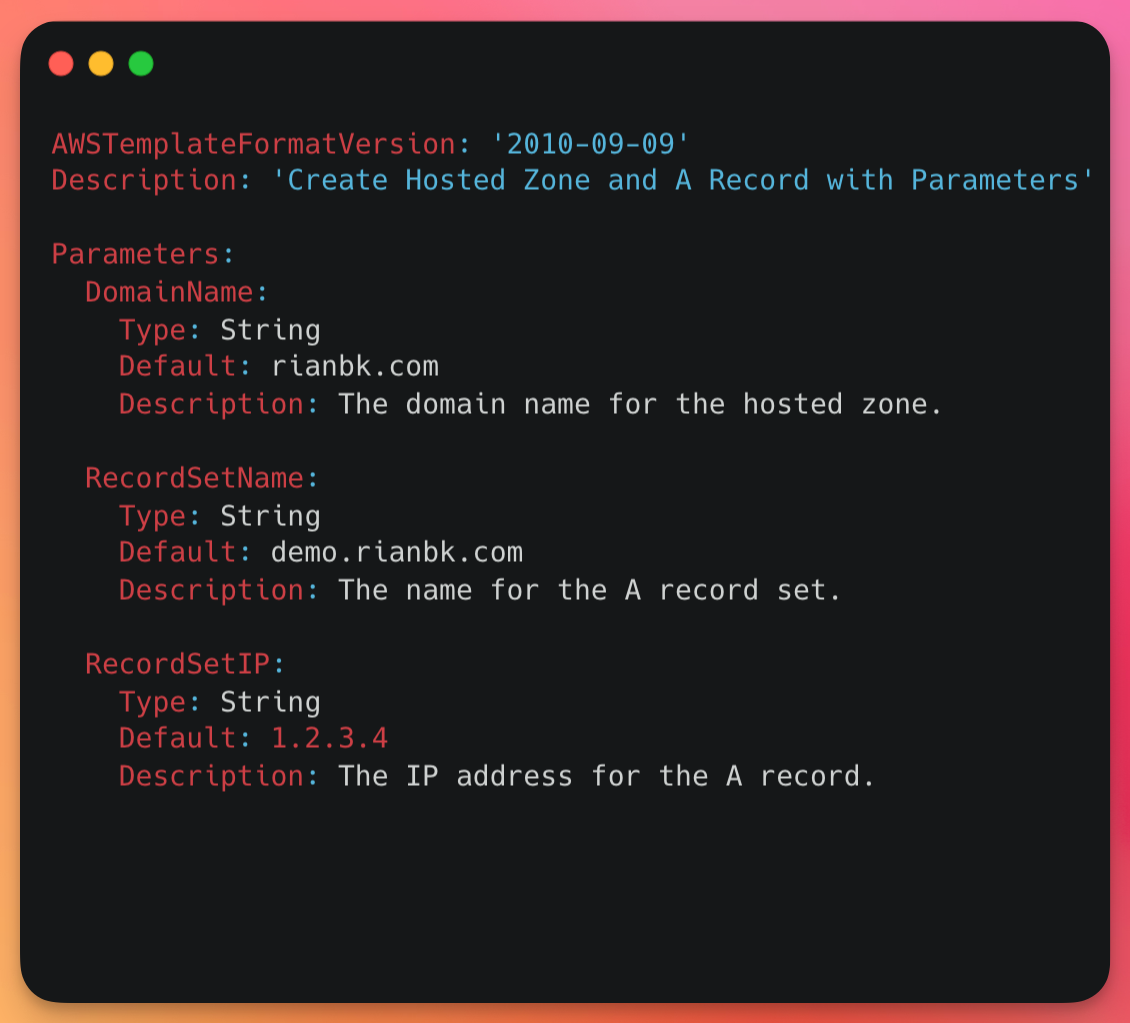
AWS has a couple of native tools for IaC, but the original and still probably the most used is AWS CloudFormation. Now I'm not going to do a deep dive on CloudFormation today, but here is the sample template we will use (and to give you an idea of what CloudFormation can do.
AWSTemplateFormatVersion: '2010-09-09'
Description: 'Create Hosted Zone and A Record with Parameters'
Parameters:
DomainName:
Type: String
Default: rianbk.com
Description: The domain name for the hosted zone.
RecordSetName:
Type: String
Default: demo.rianbk.com
Description: The name for the A record set.
RecordSetIP:
Type: String
Default: 1.2.3.4
Description: The IP address for the A record.
Resources:
HostedZone:
Type: AWS::Route53::HostedZone
Properties:
Name: !Ref DomainName
HostedZoneConfig:
Comment: Hosted zone for !Ref DomainName
ARecordSet:
Type: AWS::Route53::RecordSet
Properties:
HostedZoneId: !Ref HostedZone
Name: !Ref RecordSetName
Type: A
TTL: '300'
ResourceRecords:
- !Ref RecordSetIP
Outputs:
HostedZoneId:
Description: The ID of the created hosted zone.
Value: !Ref HostedZone
This CloudFormation template provisions a DNS-hosted zone for the domain rianbk.com within AWS Route 53. It creates an A record for the subdomain demo.rianbk.com, mapping it to the IP address 1.2.3.4.
This template includes:
- Parameters for the domain name (
DomainName), the record set name (RecordSetName), and the IP address (RecordSetIP). - A Resource section that creates a hosted zone for
rianbk.comand an A record set fordemo.rianbk.com. - An Outputs section that outputs the ID of the created hosted zone.
Introducing AWS CloudFormation Git Sync
The new Git Sync feature allows you to trigger a CloudFormation deployment straight from a tracked Git repository branch with a very simple setup and at the time of writing this supports GitHub, GitHub Enterprise, GitLab, and Bitbucket.
Weren't we able to do this already?
Yup, you're right. Deploying CloudFormation using a deployment pipeline isn't new, we've been doing this with AWS CodePipeline for a long time.
The great thing about Git Sync is if you have simple deployment use cases you can probably get away with just using Git Sync and not having to go about the processes of setting up a full-blown pipeline.
Let's setup GitSync
Go to the CloudFormation Console and Create a new Stack
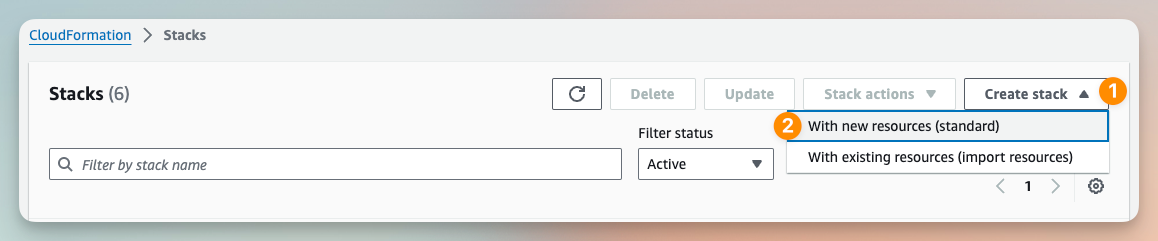
On the Create Stack page you will see a new option called Sync from Git, let's select that and click Next
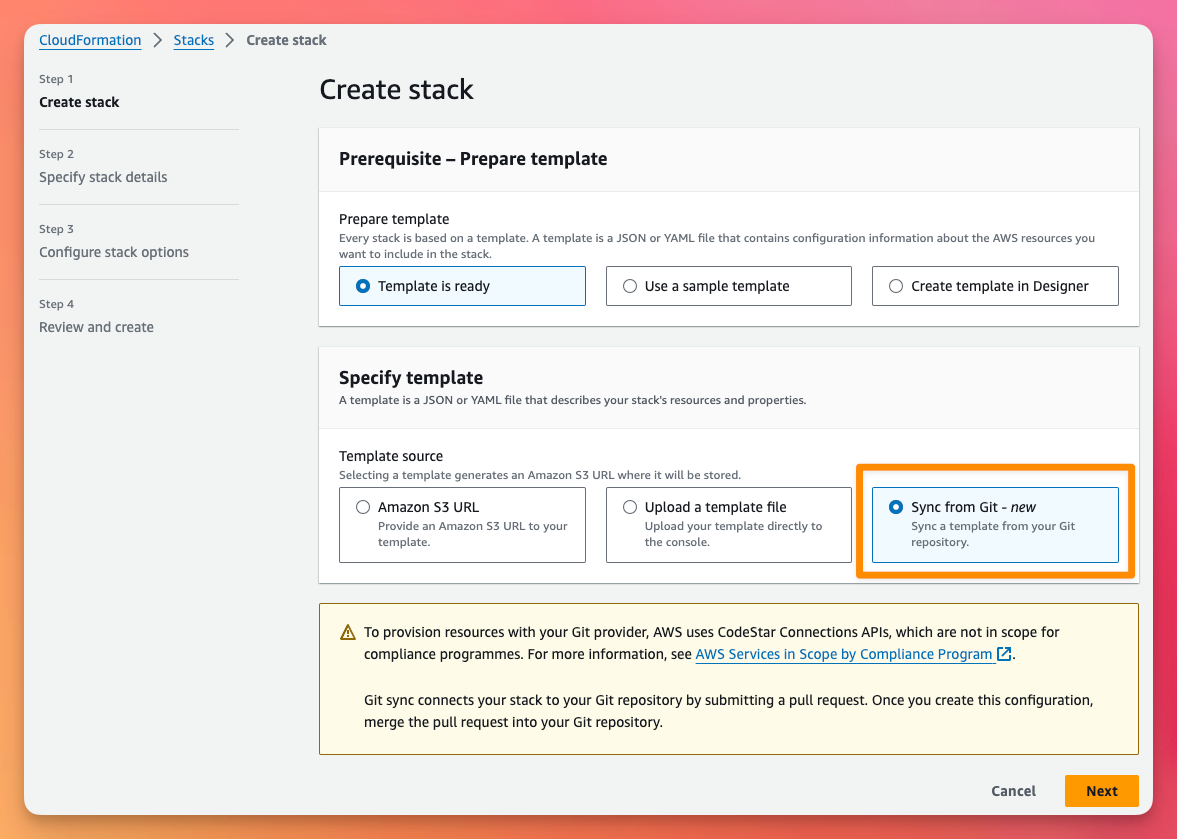
On the Stack Details page:
- Give the Stack a name
- The Deployment file is used to define parameters and values for the stack. I don't have one of these yet, so I'm going to let CloudFormation create the file.
- As this is a new configuration, I'm going to choose Link a Git repository
- I'm using GitHub today
- We need to create a connection to GitHub, so click the link Add a new connection
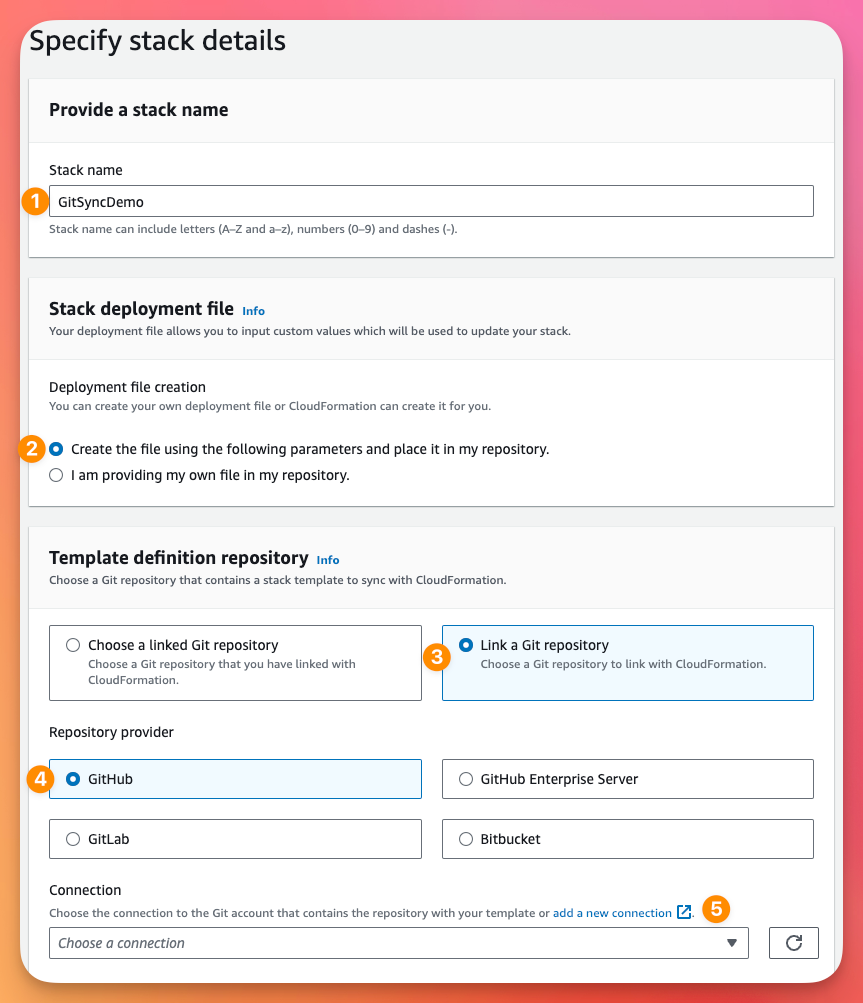
This will open a new window to the Developer Tools Dashboard (where things like CodePipeline live). Here we will select GitHub, give it a name and then click Connect to GitHub
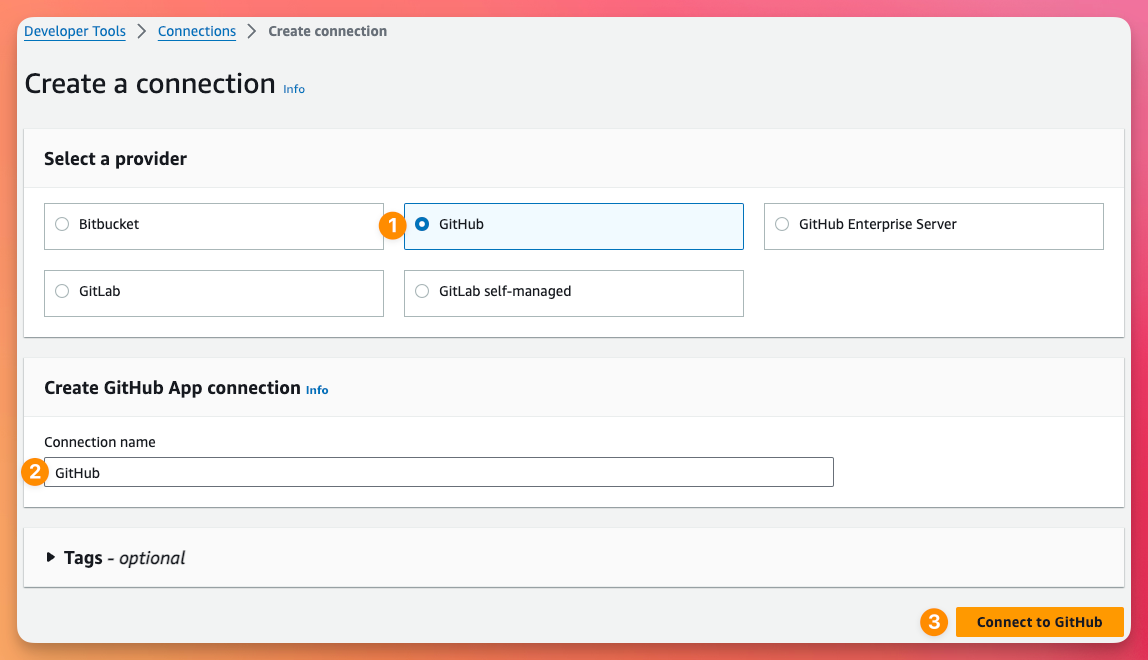
This will take you to GitHub to authorise the connection
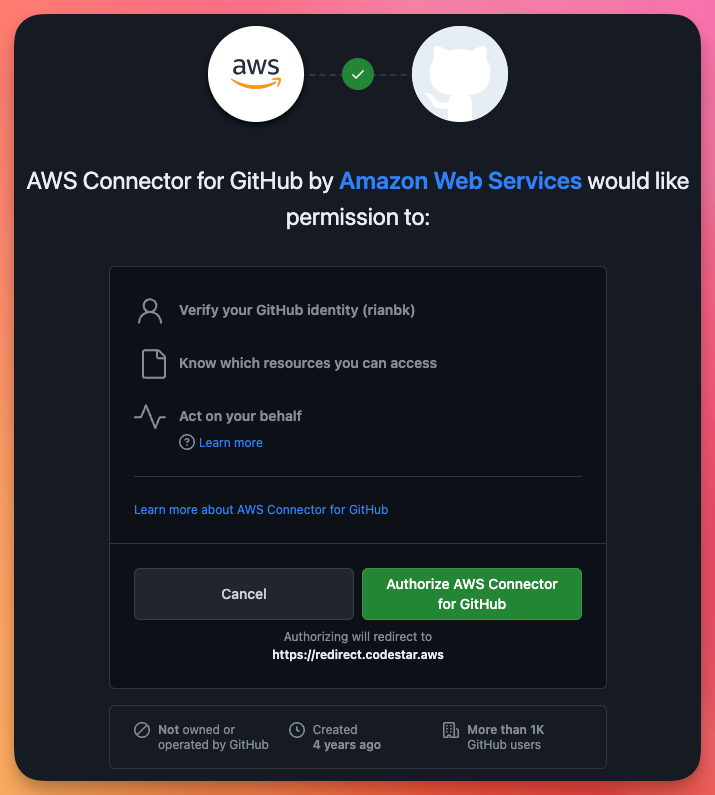
Once we authorise GitHub, this will take us back to AWS where we need to click Install a new app
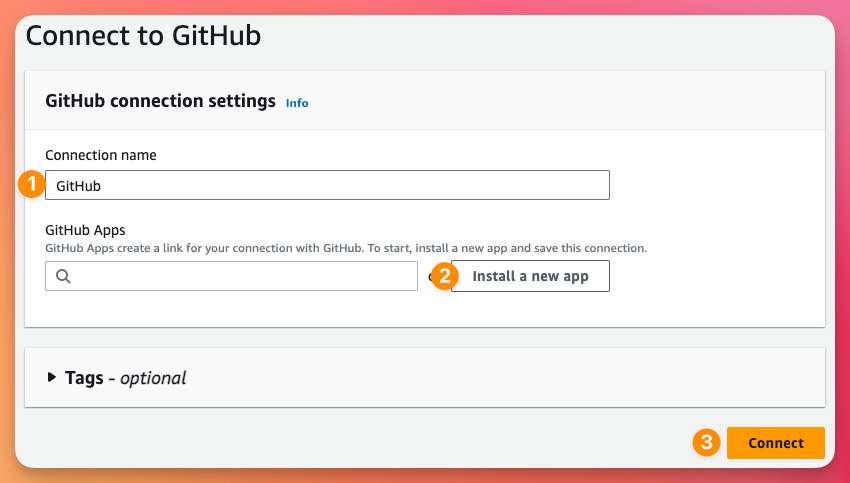
This will take us to back GitHub again so we can select the organisation we are installing the AWS Connector for GitHub too. Select the organisation you're using.

You can use this connector for other AWS Developer Services so feel free to choose the level of access that makes sense to you, I'm going to limit the access to just my demo repository, then click Install
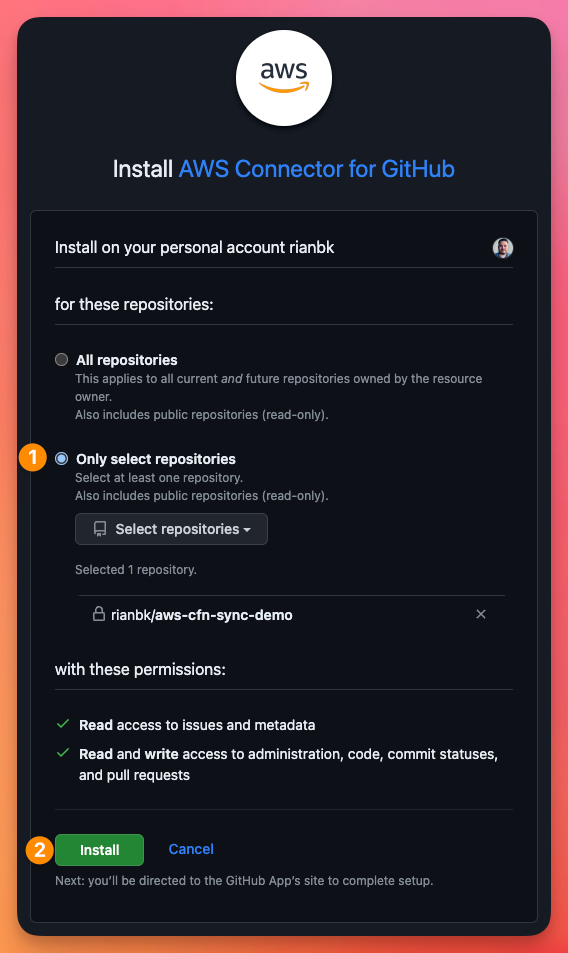
This will take you back to the AWS Connections page once again where we can see it has populated our GitHub App and we now click Connect
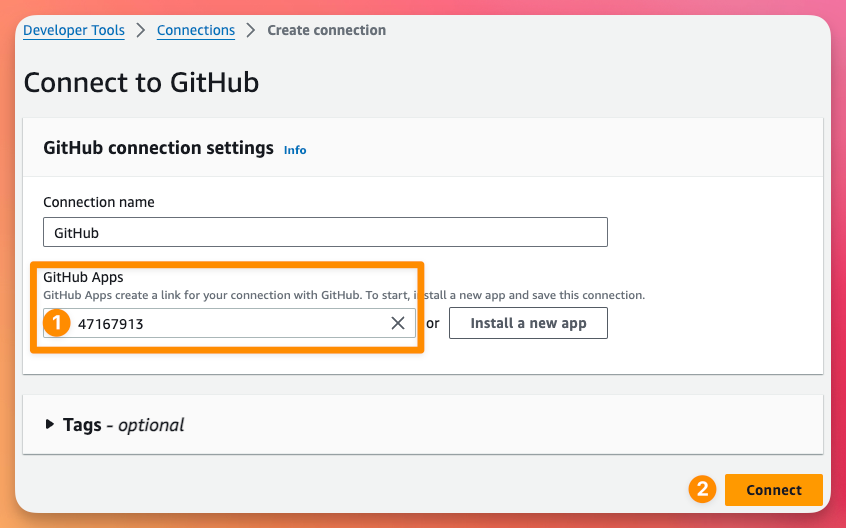
Now that our Connection is created, we can go back to the CloudFormation wizard hit refresh and select our Connection. This will then also allow us to select our Repository, Branch and give our Deployment file a name. We also need to give our IAM role a name.
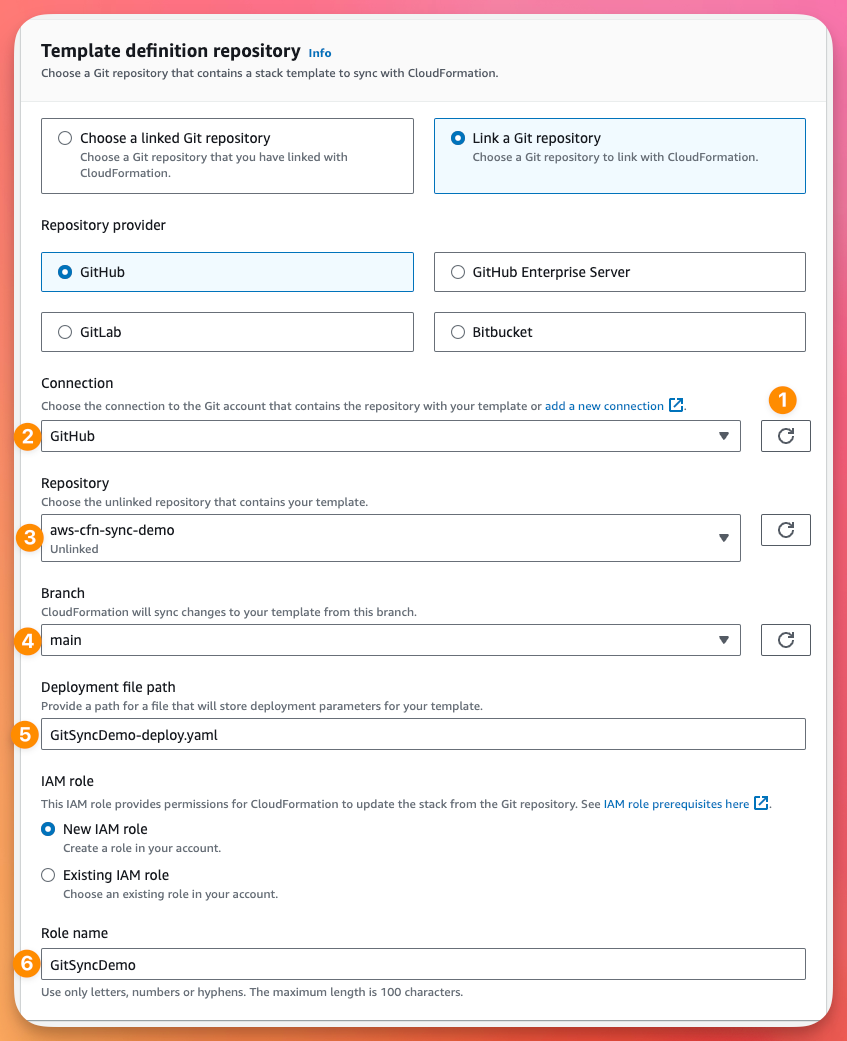
Further down the page, we need to specify our CloudFormation template file name and the Parameters that we created in the CloudFormation template before. Then we can click Next.
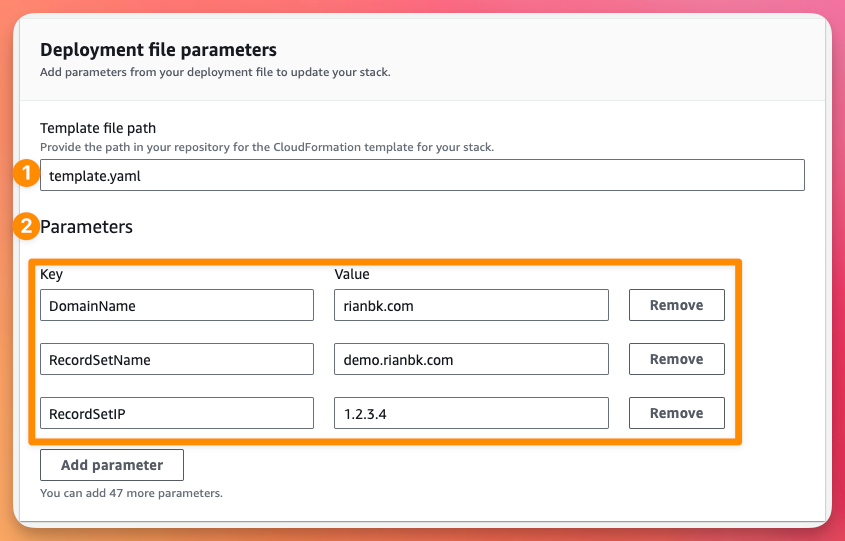
On the Stack Options page, Select an IAM Role for CloudFormation to use. I'm going to reuse a CloudFormation IAM Role I already have (if you don't have one you can find the AWS documentation for creating one here), stick with the default for the rest and click Next
Review all your settings on the Review and Create page, then hit Submit
Provisioning Status: Failed
You will notice straight away that our CloudFormation Template has already failed to provision.
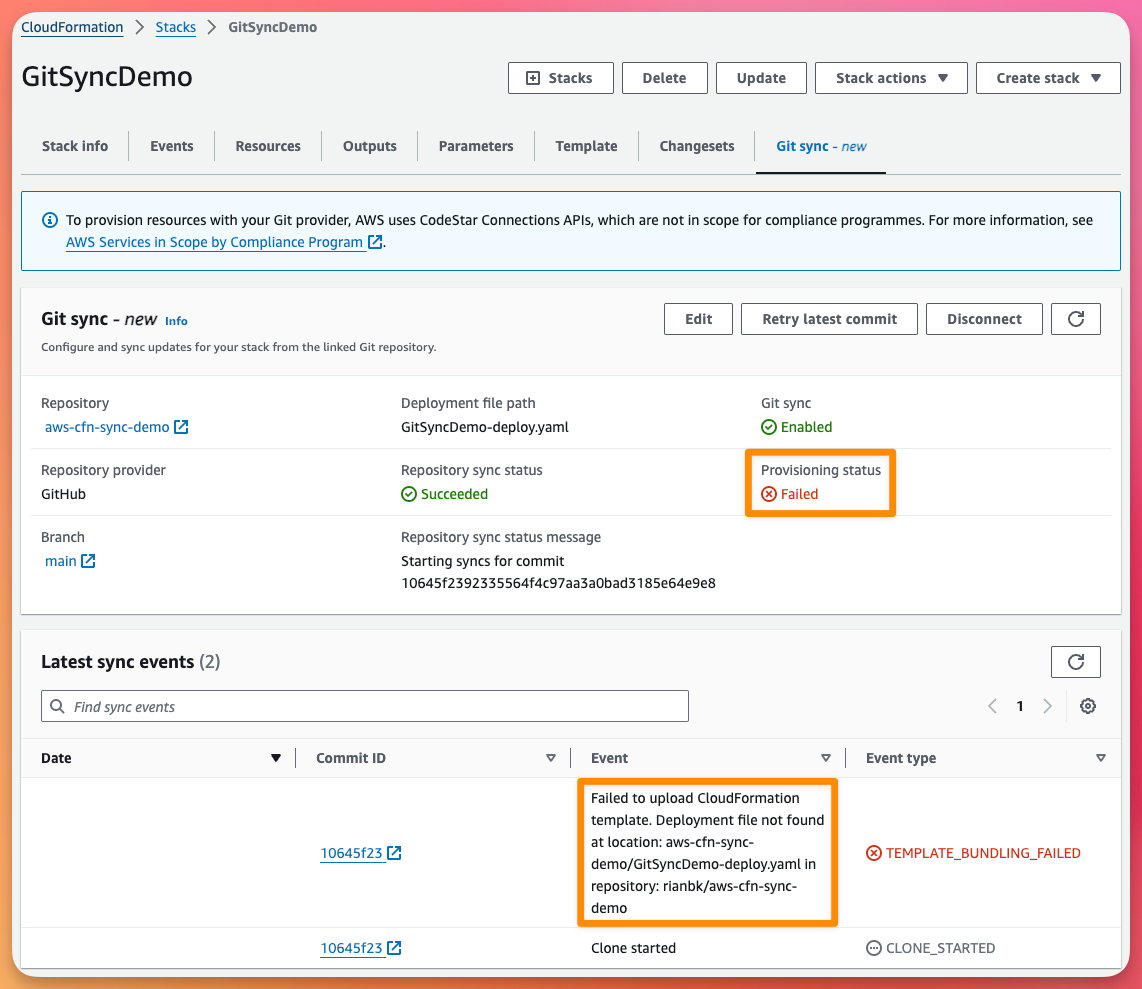
This is because the deployment configuration file can't be found in the GitHub Repository. Hang on a second, didn't we ask AWS to create this for us?
Well turns out, AWS did create it for us! AWS following best practice has created a Pull Request in our GitHub repository for us to review and merge with the main branch.
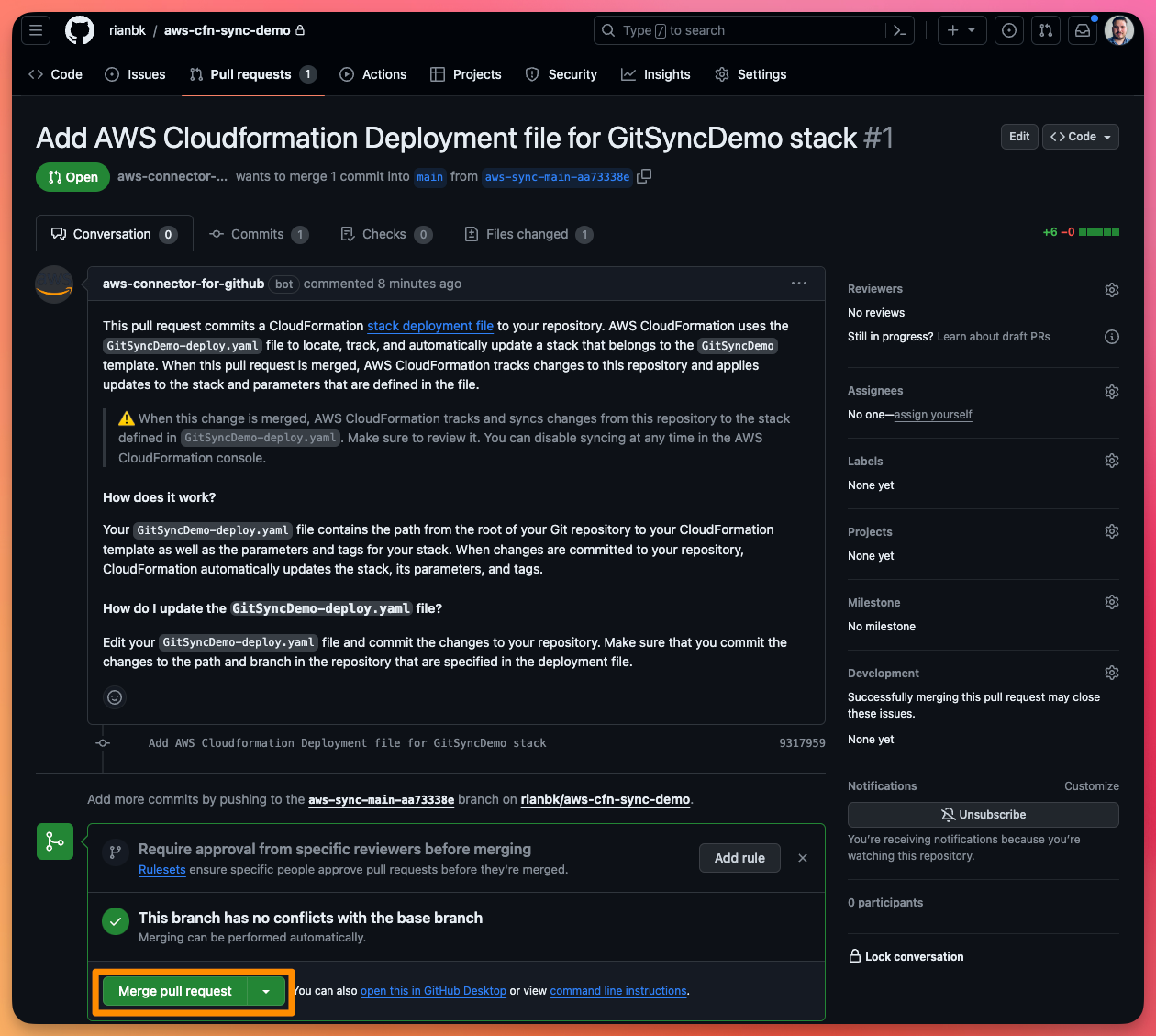
As part of this pull request, AWS created the Deployment File GitSyncDemo-deploy.yaml
template-file-path: template.yaml
parameters:
DomainName: rianbk.com
RecordSetName: demo.rianbk.com
RecordSetIP: 1.2.3.4
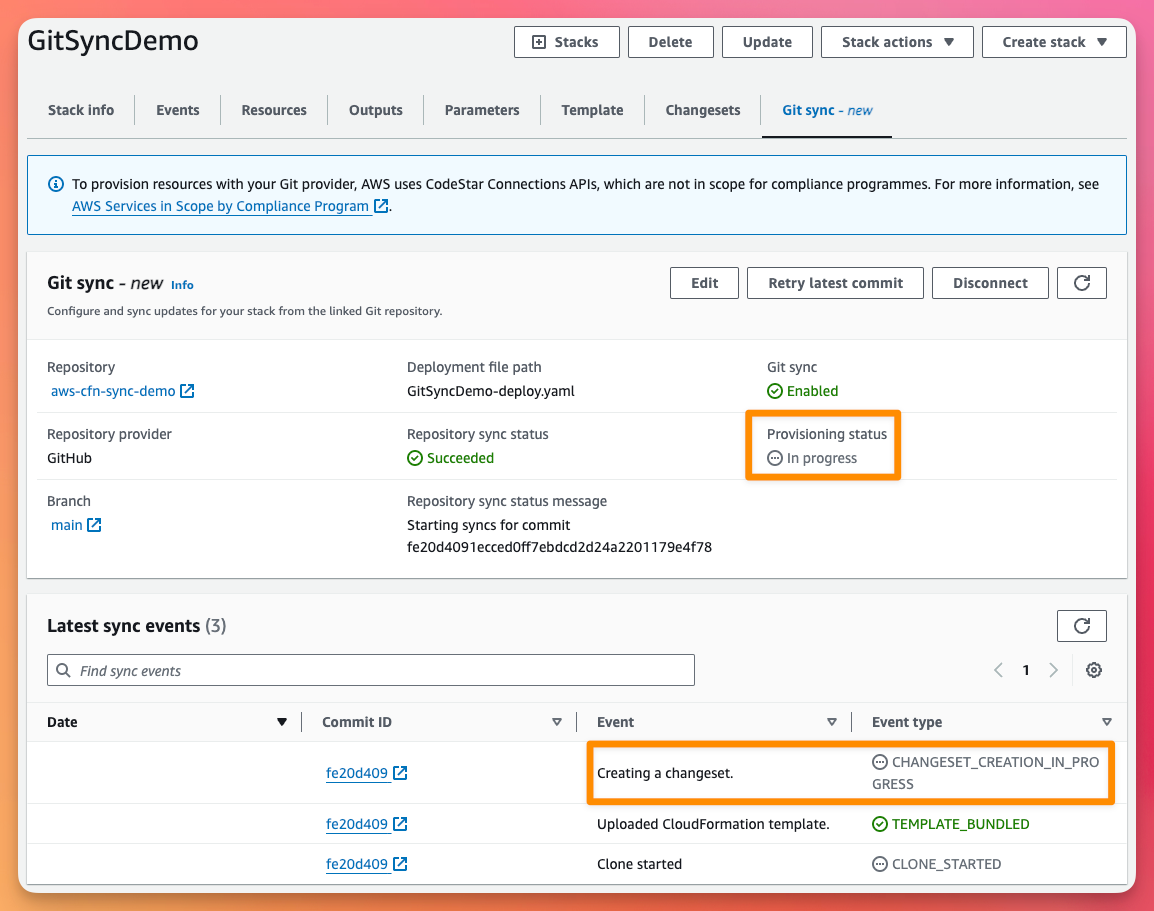
tags: {}Once we have merged the PR, we can now see that CloudFormation has automatically detected the change to the main branch, created a Change Set and started the provisioning.
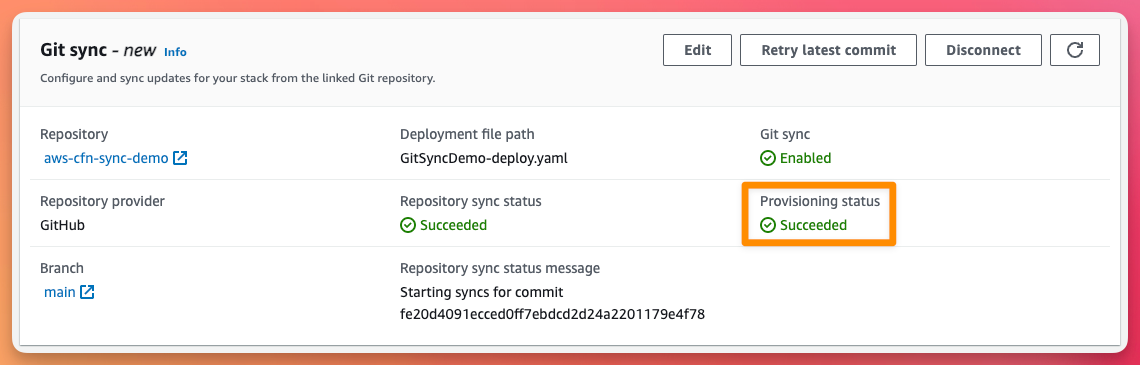
After a little while, we can now see that the provisioning is complete.
If we now go to Route53, we can see the deployed hosted zone and A record!
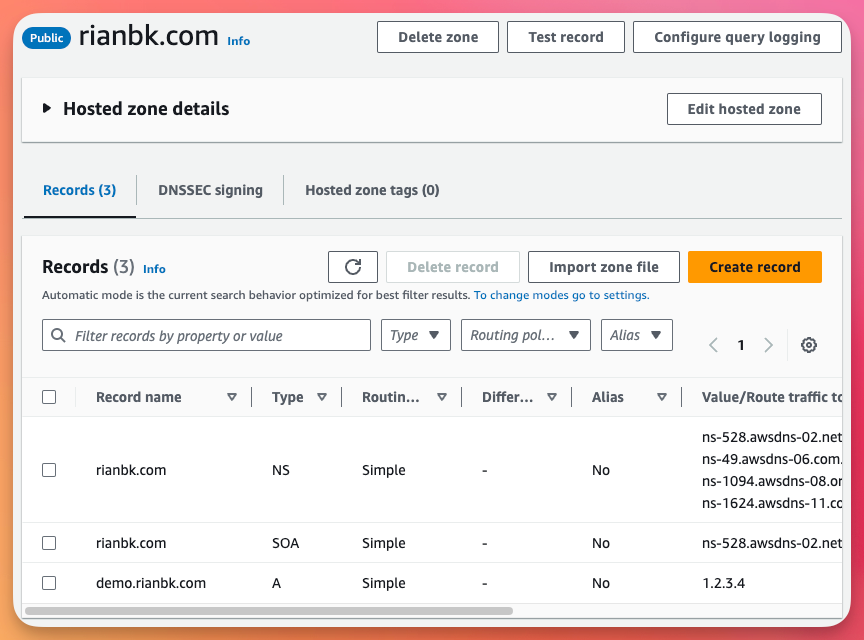
Simple CloudFormation deployments with Git Sync
In a few easy steps, we now have automated CloudFormation deployments straight from our Git repository. To update your deployment, simply create a commit with your updated deployment template, or tweak your Deployment file to change the parameters as required.
Here is the AWS documentation on CloudFormation Git Sync if you need to know more.