Secure your AWS management account with Delegated Administrator
Your AWS management account is the most important account in your AWS organisation. Learn how you can reduce the need for users accessing this account and provide least privilege access with Delegated Administrator.

When you got started with AWS, you probably just registered for an account, slapped in a credit card, and started exploring, tinkering, and building. As you started getting closer to something production ready, the thoughts about making things secure started to become a bit more of a priority.
This is a common story that I talk to people about all the time, after all, you need to get started somewhere. At this point I generally see people go a few ways, they do nothing, they secure down the account they are working in, or they look to adopt a multi account architecture. A multi-account architecture allows you to have more granular control, split out operational concerns into multiple accounts and also take advantage of the biggest security boundary that AWS has, the AWS account itself.
As a quick hint if your looking into where to get started with a multi-account architecture, one of the easiest ways to get started is to use AWS Control Tower, this is a managed service from AWS that helps automate the configuration and provides automation for provisioning and running a multi-account architecture.
The Management Account
In an AWS multi-account architecture there is one AWS account that rules over all, the Management Account. This is the account where services like AWS Control Tower run from, where all your AWS billing is consolidated to and a critical central point for security. In this account, one of the biggest security controls in an AWS multi-account architecture is configured, AWS Organisations. Organisations provides centralised management of all of your AWS Accounts and allows you centralise policy across accounts using Service Control Policies.
Service Control Policies
Service control policies (SCPs) are one of the most powerful security functions within AWS. They allow you to define guardrails on what actions that can be done within all of your AWS accounts. No matter what permissions are given to someone within in AWS account using IAM. Service Control Policies have the final say if that person can carry out that action.
- Want to restrict what region or services people can use across your organisation?
- Want to prevent people from disabling security controls? Want to enforce tagging? SCPs are the way to do it. SCPs can even control what the root user in an AWS account can do (in the member accounts)
This brings us full circle back to the management account and why multi account architectures are important.
Service Control Policies cannot apply to the management account in an AWS Organisation.
Why? AWS doesn’t want you to be able to lock yourself out of your entire AWS ecosystem, and with SCPs, you absolutely could if you wanted too. This is why it is super important that you don’t operate any resources inside the management account (as you won't be able to use SCPs to control the users or roles working with them), and you heavily restrict who can have access to the management account.
Introducing Delegated Administrator
This is where the Delegated Administrator functionality of AWS Organisations can really help, and I think is a feature that not a lot of people realise exists.
When you select a member account to be a Delegated Administrator for a service in your organisation. Users and Roles in that selected member account can carry out actions for that service that can usually only be done by users or roles in the management account. This allows you to further restrict who needs access to the management account but also provides administrative functions from accounts that make sense, for example delegating security service management to your central security account.
Another great example is configuring Delegated Administrator for AWS CloudFormation StackSets.
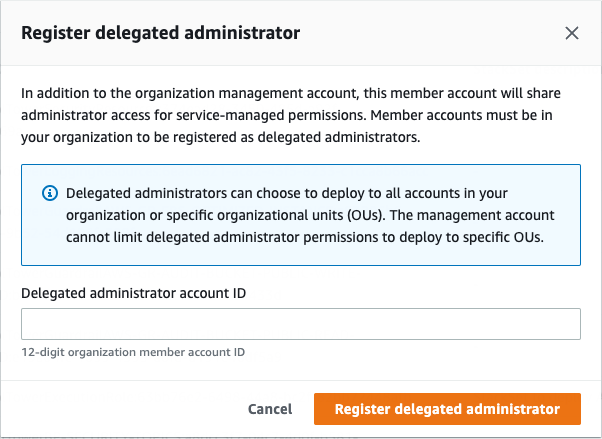
This allows you to enable your users to deploy CloudFormation StackSets across your organisation and accounts without needing to give them access to the management account.
Supported Services
At the time of writing, Delegated Administrator is supported by the following AWS Services:
- AWS Account Management
- AWS Audit Manager
- AWS CloudFormation StackSets
- AWS Config
- Amazon Detective
- Amazon DevOps Guru
- AWS Firewall Manager
- Amazon GuardDuty
- IAM Access Analyzer
- Amazon Inspector
- AWS License Manager
- Amazon Macie
- AWS Network Manager
- AWS Security Hub
- Amazon S3 Storage Lens
- AWS Service Catalog
- AWS IAM Identity Center (successor to AWS Single Sign-On)
- AWS Systems Manager
- Amazon VPC IP Address Manager (IPAM)
You can also view the up to date list here in the AWS Organisations documentation.
Go forth and delegate
Hopefully this gives you some insight into Delegated Administrator, and you can look to implement it within your environment, further securing your management account and enabling your administrators.